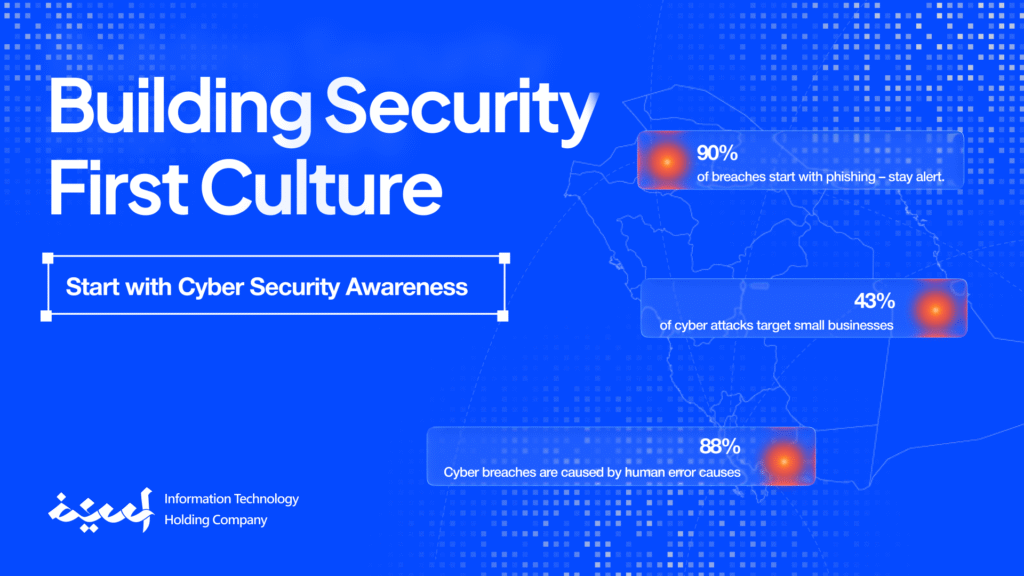
- ARTICLE
Stay Secure with a Trusted Cybersecurity Consultant
Discover how cyber security consultants help Saudi businesses stay secure & compliant. Learn about risks, solutions, and the cybersecurity consultant roadmap.
Discover how cyber security consultants help Saudi businesses stay secure & compliant. Learn about risks, solutions, and the cybersecurity consultant roadmap.
Introduction
Cyber security consultant services have become essential in Saudi Arabia’s Vision 2030 digital journey. As businesses embrace cloud solutions, AI-driven platforms, and interconnected infrastructure, threats like phishing, ransomware, and data breaches are no longer rare. These attacks impact far more than IT systems, disrupting operations, damaging reputations, and attracting regulatory penalties.
Unlike traditional IT teams, a cyber security consultant brings specialized expertise to prevent attacks and ensure compliance with Saudi regulations such as the SAMA Cybersecurity Framework and the NCA Essential Cybersecurity Controls (ECC). In today’s fast-changing threat landscape, proactive cybersecurity is not optional but it’s the foundation of resilience, trust, and sustainable business growth.
Who Is a Cyber Security Consultant?
Defining the Role of a Cyber Security Consultant
A cyber security consultant is a specialized professional dedicated to protecting organizations from evolving digital threats. Unlike general IT staff who focus on system maintenance, a consultant provides expert guidance on identifying risks, securing networks, and ensuring compliance with strict cybersecurity regulations.
Their role combines technical expertise, regulatory knowledge, and strategic planning. By assessing vulnerabilities, designing defense frameworks, and training employees, cyber security consultants act as trusted advisors who help businesses stay secure and resilient in a rapidly changing threat landscape.
Download Your Cybersecurity Readiness Scorecard
Evaluate your cybersecurity readiness and uncover key risks.

What Does a Cyber Security Consultant Do?
Core Responsibilities of a Cyber Security Consultant
A cyber security consultant is a trained expert who helps organizations identify weaknesses, strengthen defences, and safeguard digital operations. Unlike in-house IT teams focused on daily maintenance, consultants bring an external, unbiased perspective rooted in global best practices and local regulations.
Key Responsibilities of a Cyber Security Consultant:
Performing Risk Assessments
Evaluating networks, applications, and systems for vulnerabilities ranging from outdated software to weak password policies.
Designing and Implementing Security Solutions
Building tailored defence systems, including firewalls, intrusion detection, endpoint protection, and encryption.
Ensuring Regulatory Compliance
Aligning operations with frameworks like SAMA, NCA ECC, and ISO 27001 to avoid penalties and strengthen trust.
Conducting Penetration Testing
Using ethical hacking techniques to simulate real-world attacks and expose exploitable gaps.
Creating Incident Response Plans
Developing structured playbooks so teams can react quickly and minimize damage during a breach.
Training Internal Teams
Delivering workshops and simulations to reduce human error i.e. one of the top causes of breaches.

Why Every Sector in Saudi Arabia Needs a Cyber Security Consultant?
How Cyber Security Consultants Protect Different Industries
In Saudi Arabia’s rapidly digitalizing economy, no industry is immune to cyber threats. Each sector faces unique risks, compliance requirements, and attack surfaces. A cyber security consultant helps businesses navigate these challenges by tailoring strategies to their specific environment, whether that means safeguarding payment systems, protecting patient data, or securing critical infrastructure.
Retail & E-Commerce
Retailers and online merchants handle massive volumes of customer and payment data, making them attractive targets for fraud and cyberattacks.
- Risks: credit card fraud, bot traffic, loyalty program abuse, and web application attacks.
- Consultant Role: PCI DSS compliance audits, securing POS and online checkout systems, implementing fraud detection tools, and delivering phishing-prevention training to staff.
Healthcare
Hospitals and clinics deal with sensitive patient records and increasingly rely on IoT/IoMT devices, many of which lack robust security. A single breach can compromise safety and trust.
- Risks: ransomware, EMR (Electronic Medical Record) breaches, and connected medical device exploits
- Consultant Role: designing HIPAA/NCA-aligned frameworks, implementing endpoint and network security, enforcing role-based access, and preparing incident response playbooks.
Start-ups & Tech Companies
Fast-moving fintech, SaaS, and AI start-ups often prioritize speed to market over security, leaving them vulnerable.
- Risks: cloud misconfigurations, insider threats, and lack of compliance awareness.
- Consultant Role: performing vulnerability assessments, securing DevOps pipelines, integrating compliance (SAMA, ISO 27001) from day one, and building secure authentication systems.
As Saudi Arabia continues to expand its industrial base, OT/IT convergence and legacy systems open the door to sophisticated attacks, including state-sponsored espionage.
- Risks: SCADA attacks, unpatched legacy systems, third-party vendor breaches.
- Consultant Role: securing SCADA/ICS environments, conducting supply chain risk assessments, performing air-gapped network audits, and ensuring compliance with critical infrastructure regulations. Read more on the Saudi Aramco $50M data breach.
Government Contractors & Public Sector Vendors
With high compliance standards and sensitive data, public sector vendors are frequent targets of advanced threats.
- Risks: APTs (Advanced Persistent Threats), regulatory non-compliance, supply chain vulnerabilities.
- Consultant Role: guiding compliance with NCA ECC and SAMA frameworks, conducting third-party vendor risk assessments, enhancing endpoint/cloud security, and creating audit-ready documentation.
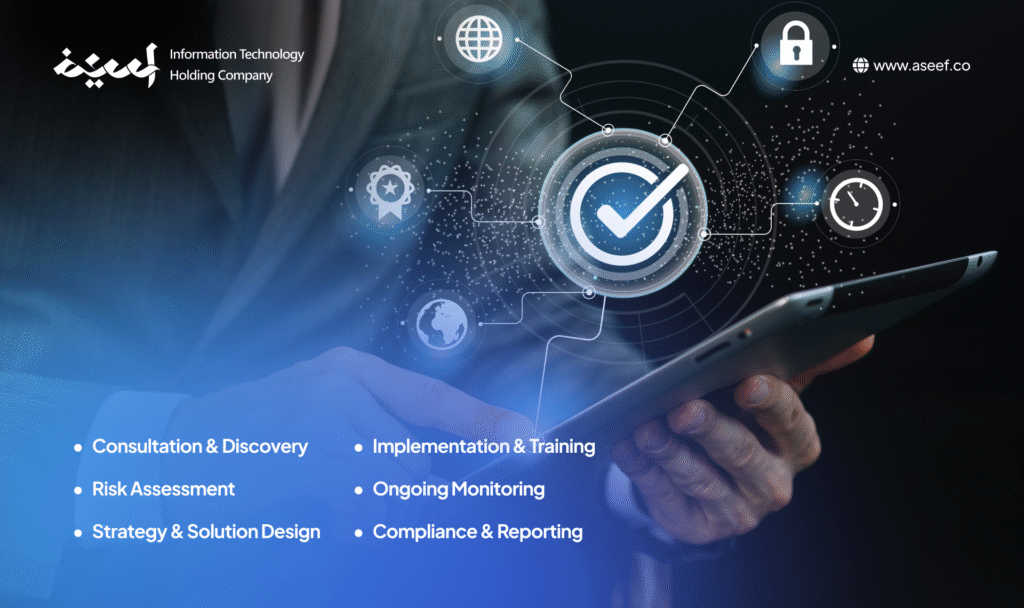
The Cybersecurity Consulting Process: From Assessment to Protection
The Roadmap of a Cyber Security Consultant
A cyber security consultant does not simply install a firewall or suggest antivirus software. They use a rigorous, multi-step process aimed at evaluating, solidifying, and maintaining an organization’s posture with regard to security while complying with local and international regulations.
Here’s how a typical cybersecurity consulting engagement unfolds:
The Cybersecurity Consulting Process: A Quick Overview
1. Consultation & Discovery
Begins with understanding your business model, infrastructure, compliance needs (e.g., SAMA, NCA), and current policies to define the scope.
2. Risk Assessment
Identifies technical gaps, network vulnerabilities, insider threats, and employee awareness issues often through penetration testing.
3. Strategy & Solution Design
A tailored roadmap is created covering security architecture, data protection, compliance alignment, and incident response planning.
4. Implementation & Training
Consultants help deploy solutions, integrate with existing systems, and train staff to reduce human error and improve cyber hygiene.
5. Ongoing Monitoring
Includes real-time threat detection, SIEM setup, and regular scans to ensure continuous protection against evolving threats.
6. Compliance & Reporting
Detailed documentation is maintained for regulators (e.g., SAMA, NCA), IT teams, and executive leadership to support audits and decisions.
Conclusion
Don’t Wait for a Breach, Be Proactive with Expert Guidance
In Saudi Arabia’s fast-moving digital economy, cybersecurity is a pillar of business continuity, not an afterthought. A skilled cyber security consultant helps identify risks, build robust defences, and ensure compliance with SAMA, NCA, and ISO standards.
By taking a proactive approach, businesses avoid costly breaches, strengthen readiness, and protect their reputation in a highly competitive market. The best time to secure your future is now.
The best time to secure your future is now. Consult our cyber security expert today and take the first step toward stronger protection.
Blog Summary
Saudi Arabia’s digital transformation brings vast opportunities and serious cyber risks. As cyberattacks grow in volume and complexity, businesses need more than just IT, they need cybersecurity consultants to ensure both protection and compliance. A trusted consultant helps you stay ahead of threats while aligning with SAMA and NCA regulations.
A cyber security consultant identifies vulnerabilities, designs protection strategies, ensures regulatory compliance, and trains your team to reduce human error. Their role includes conducting risk assessments, penetration testing, and creating incident response plans. At Aseef, our consultants offer Saudi-specific, certified expertise to help local businesses stay secure and compliant.
Different sectors in Saudi Arabia face unique risks—from payment fraud in retail to SCADA breaches in industry. Consultants help tailor solutions for each sector, such as PCI audits for e-commerce, HIPAA-aligned frameworks for healthcare, and NCA compliance for public contractors. Their value lies in sector-specific knowledge and proactive defenses.
Cybersecurity consulting follows a structured process: discovery, risk assessment, strategy development, implementation, monitoring, and compliance reporting. Consultants align security strategies with Saudi regulatory frameworks while educating staff and maintaining readiness. The goal is not just defence but long-term resilience and audit-readiness.
Frequently Asked Questions (FAQs)
1. What is a cyber security consultant and why is one important for businesses in Saudi Arabia?
A cyber security consultant helps businesses prevent cyber threats and meet regulations like SAMA and NCA. They’re crucial for protecting digital operations in Saudi Arabia’s growing digital economy.
2. What are the most common cyber threats faced by Saudi businesses today?
Phishing, ransomware, cloud misconfigurations, SCADA attacks, and third-party breaches are among the top risks.
3. Why Organizations Hire Consultants?
Consultants offer expertise, tailored solutions, industry best practice recommendations, and are critical especially for organizations lacking in-house cyber security staff.
4. How do cyber security consultant services differ from internal IT teams?
Consultants bring outside expertise, unbiased audits, and specialized skills your in-house IT may lack.
5. What’s included in a typical cyber security consulting engagement?
Assessment, planning, implementation, team training, monitoring, and compliance documentation.
6. What certifications or experience should a cyber security consultant have?
Look for CISSP, CISM, CEH, or ISO 27001 certifications, plus experience with Saudi frameworks like SAMA and NCA.
Publication Date
Category
- Cyber Security
Table of Contents
Ready to Transform?
Whether you’re starting your digital journey or scaling transformation, Aseef is your reliable IT consulting company in Saudi Arabia.