- ARTICLE
Cyber Security Attacks: Top Business Defenses for 2025
Understand the latest cyber security attacks targeting Saudi companies and how to defend your business with modern, multi-layered strategies.
Understand the latest cyber security attacks targeting Saudi companies and how to defend your business with modern, multi-layered strategies.
Introduction
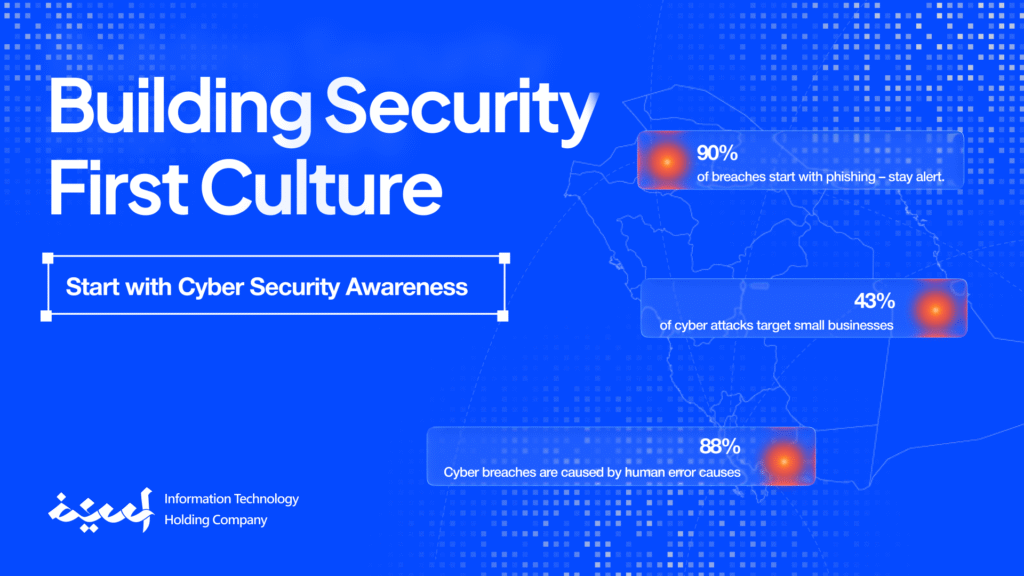
Cyber security attacks are growing at an unprecedented pace. A recent report predicts global cybercrime costs will reach $10.5 trillion annually by 2025 (Cybersecurity Ventures). In Saudi Arabia, businesses undergoing rapid digital transformation from SMEs to large enterprises are prime targets.
From ransomware that locks critical data to phishing (التصيد الاحتيالي) scams in Arabic, the threats are diverse and increasingly complex. At Aseef, we’ve worked with start-ups, corporates, and government contractors across the Kingdom, witnessing first hand how devastating an unprepared approach to cyber security can be.
This guide explores the most common cyber security attacks in Saudi Arabia, their impacts on businesses, and the practical solutions you can adopt to stay protected.
What Are Cyber Security Attacks?
Understanding Cyber Security Attacks and Their Targets
Cyber security attacks are deliberate attempts by hackers or cybercriminals to infiltrate digital systems; networks, cloud platforms, or applications with the goal of stealing information, causing disruption, or gaining financial advantage.
Examples include:
- Phishing emails that trick employees into sharing passwords.
- Ransomware that locks business files until payment is made.
- Denial-of-Service (DoS) attacks that crash ecommerce websites.
Importantly, these attacks don’t just target large corporations. In Saudi Arabia, SMEs, hospitals, fintech companies, and even retailers are increasingly being hit. With more reliance on cloud-based ERPs, mobile apps, and online payments, attackers exploit every weak link.
For a deeper understanding, see IBM’s Cyber Attack overview.
Why Do Cyber Security Attacks Happen?
Why Cyber Security Attacks Occur: Main Motives and Weaknesses
Cyber security attacks happen because attackers see an opportunity to benefit usually by stealing money, data, or access. For example, they might want to get credit card details, trade secrets, or personal information that can be sold on the dark web. In other cases, hackers use ransomware to demand payment or carry out attacks to cause disruption and gain attention.
Another big reason is weak security practices. Businesses with outdated software, poor password management, or untrained employees become easy targets. Sometimes attacks also happen for political reasons, espionage, or just to exploit vulnerabilities in new technologies like cloud systems or mobile apps. In short, cyber attacks occur wherever there’s value to gain and weak defences to exploit.

Which Cyber Security Attacks Pose Threat to Companies?
Common Motives Behind Cyber Security Attacks
As Saudi Arabia’s digital growth accelerates, cyber attackers are increasingly targeting businesses with outdated systems and weak endpoint security. Low awareness and poor protection measures are putting both the public and private sectors at rising risk.
1. Phishing Attacks (Email & SMS Fraud in Arabic)
Attackers often send fake messages to trick people into clicking harmful links, downloading dangerous files, or sharing sensitive information. Since many businesses don’t provide proper cybersecurity training, their employees become easy targets for these scams.
2. Ransomware Attacks
These attacks encrypt your data and demand payment, often in cryptocurrency, to release it. They’re increasingly targeting logistics, healthcare, education, and even government contractors.
3. Distributed Denial of Service (DDoS)
DDoS attacks flood your website or servers with traffic until they crash, taking down ecommerce platforms, payment portals, or mobile apps during peak sales. The common targets are Ecommerce startups, payment gateways, and online booking platforms.
4.AI-Powered Credential Stuffing
With AI, attackers can test thousands of stolen passwords every minute, putting businesses without multi-factor authentication (MFA) at high risk. Reusing the same passwords across ERP, HR, and accounting systems makes cloud logins even more vulnerable. As AI in business grows, so does its misuse by attackers making strong security a must.
5. API & ERP Exploits
Hackers often target weak APIs in cloud systems, apps, and ERPs. If left unpatched, these flaws can leak sensitive data, putting businesses at high risk especially when digital tools are adopted without regular security audits.
6. Insider Threats
Careless or malicious insiders are responsible for an increasing share of cyber security incidents. This could be an employee falling for a phishing scam, or intentionally leaking sensitive data.

What Happens When You’re Not Prepared: The Real Cost of a Cyber Security Attack
The Real Cost of Cyber Security Attacks on Businesses
For many Saudi businesses, the assumption is: “It won’t happen to us.” But in today’s hyper-connected ecosystem, a single weak point can trigger massive operational, financial, and reputational damage, especially in sectors under active digital transformation.
Here’s what a typical cyber security attack looks like for an unprepared business:
1. Financial Losses
Cyber security attacks like ransomware, data breaches, and DDoS cause costly downtime, recovery expenses, legal fees, and fines. For digital-heavy industries, even short disruptions make proactive cybersecurity a smart investment.
According to Arab news, cybercrime damages are expected to reach $10.5 trillion, with businesses losing up to 10% in revenue due to attacks. Saudi experts stress the need for proactive security measures and skilled cyber security analysts to prevent costly disruptions and ensure long-term resilience.
2. Business Disruption
Cyber attacks can disrupt critical systems like customer support, payments, ERP, and cloud processes halting operations and damaging customer trust. Even brief outages can lead to delivery delays, payment failures, and lasting reputational harm, especially for businesses that rely on seamless digital workflows.
3. Data Breach Consequences
Data breaches bring fines, lawsuits, lost contracts, and reputational damage. Protecting sensitive data is vital not just for compliance, but for long-term business trust and continuity.
The Saudi Aramco breach exposed over 1TB of sensitive data through a third-party contractor, not Aramco’s own systems. This incident highlights the growing risk of supply chain attacks and the need for businesses to assess vendor security and adopt a Zero Trust approach.
4. Reputational Damage
A public cyber incident can seriously harm a company’s reputation, especially in trust-driven markets like the GCC. It can lead to lost customers, strained partnerships, and investor doubt. Rebuilding trust takes time and in some cases, the damage may be permanent.
5. Psychological and Team Impact
A cyber attack impacts more than just systems, it puts immense pressure on your IT team, leadership, and staff. Without a clear response plan, confusion and delays can worsen the damage, lower morale, and erode trust. Preparing your team mentally and operationally is as crucial as having the right technical safeguards..

What are the Effective Ways to Protect Your Business from Cyber Security Attacks?
Best Ways to Defend Against Cyber Security Attacks
Cyber security attacks are a constant threat, but their damage can be avoided. With the right strategy and tools, your business can stay protected. At Aseef, we design scalable cybersecurity solutions tailored to your size, industry, and systems, keeping you safe in today’s digital world. A trusted cyber security consultant can further strengthen your defences and keep you ahead of attackers. Here are some of the most effective ways to protect your business from cyber security attacks.
1. Implement Multi-Layered Security Architecture
Security shouldn’t depend on one tool or team. You need protection across:
- Network (firewalls, intrusion detection)
- Application layer (API & ERP security)
- Endpoint (employee devices, mobile apps)
- Cloud platforms (AWS, Azure, etc.)
2. Launch Cyber security Awareness Training
Your employees are your first line of defense. Regular training helps prevent:
- Phishing and social engineering attacks
- Password mishandling
- Unintentional data leaks
3. Conduct Regular Security Audits and Penetration Testing
Frequent vulnerability scans and ethical hacking simulations:
- Identify gaps in your digital environment
- Test how your systems respond to real-world threats
- Ensure compliance with NCA and PDPL standards.
4. Enable Real-Time Monitoring and Threat Detection
Use AI-powered tools and Security Operations Center (SOC) services to:
- Detect suspicious activities instantly
- Isolate infected systems quickly
- Respond to threats before damage escalates
5. Enforce Strong Access Controls & MFA
Protect critical data by:
- Limiting access to “need-to-know” users
- Using Multi-Factor Authentication (MFA) across all systems
- Managing third-party access for cloud apps or ERP
6. Backup Data Securely And Test Recovery
Daily or weekly backups aren’t enough. Ensure:
- Encrypted backups (stored offline or in secure cloud)
- Tested disaster recovery protocols
- Ransomware rollback capabilities
Download Your Cybersecurity Readiness Scorecard
Evaluate your cybersecurity readiness and uncover key risks.
Creating a Cyber Defence Roadmap for Your Saudi Business
Step-by-Step Cyber Defence Roadmap for Saudi Businesses
Cyber security resilience is something that develops over time and needs to expand in sync with your digitalization. We assist Riyadh businesses and others in creating industry-specific, scale-specific, and maturity-specific cyber defence plans at Aseef.
Cyber Defence Roadmap for Saudi Businesses
Step 1: Cyber Risk Assessment


Step 2: Regulatory Alignment


Step 3: Build Your Security Stack


Step 4: Team Training & Awareness


Step 5: Real-Time Monitoring & Incident Response


Step 6: Continuous Testing & Audits


Step 7: Quarterly Review & Strategic Upgrade


Ready to strengthen your defenses? Book a Cybersecurity Consultation with Aseef today.
Case Study: Building a Secure & Scalable Investment Platform for Centurion Invest
Real-World Example: Strengthening Cyber Security for a Fintech Platform
Centurion Invest operates in the dynamic digital asset management sector. With the growing shift toward online trading and portfolio tracking, the company wanted to elevate its digital presence. Their vision was to offer a seamless, secure, and insightful platform that catered to both new and experienced investors.
Objective
The goal was to create a web application that allowed users to manage their portfolios in real time, perform secure transactions, access personalized analytics, and stay informed with live market insights. The platform had to be scalable, responsive, and fully aligned with regulatory standards while reinforcing trust in the brand.
Challenges
Developing a fintech product came with challenges such as processing live financial data securely, designing a user-friendly interface for complex investment tools, and integrating third-party data providers. Centurion Invest also required strong encryption, user access control, and compliance readiness all while ensuring top-tier performance during market fluctuations.
Solution
We adopted a modular development strategy that allowed scalability and flexibility. Starting with user-focused wireframes, we designed an intuitive interface that made complex data easily understandable. The dashboard offered real-time asset tracking, interactive charts, and smart filters, all accessible across devices.
Impact
The new platform significantly improved customer engagement—especially among younger, tech-savvy investors. Transactions became faster and more reliable, while the secure environment boosted client confidence. Zero post-launch security incidents reinforced the effectiveness of our strategy, and the client reported a 30% increase in platform activity within three months.
Conclusion
Secure Your Growth Before It’s Too Late
Cyber security is no longer just about technology; it’s now a key business priority. Whether you run a growing start-up, manage important ERP data for a retail store, or handle customer information in a service company, the risks are serious, and the cost of doing nothing keeps rising.
At Aseef, we’ve helped businesses across Saudi Arabia stop ransomware and phishing attacks before they spread, build multi-layered security frameworks, and train teams to act confidently under pressure. Our expertise also ensures full compliance with national regulations like NCA and PDPL.
Secure your organization today, reach out to Aseef for a consultation and take the first step toward stronger cyber resilience.
Blog Summary
Cyber security attacks in Saudi Arabia are accelerating with digital transformation, impacting SMEs, corporates, and government contractors alike. Threats like ransomware, phishing, and cloud breaches are becoming more frequent and complex. This guide explores common attacks, their impact, and practical solutions to protect your business.
Saudi businesses face phishing, ransomware, DDoS, AI-powered brute force, and API exploits in 2025. Insider threats and physical attacks on hardware are also on the rise. Weak awareness and poor defenses make companies easy targets in this evolving landscape.
Cyber attacks cause financial losses, operational disruption, and legal penalties for unprepared businesses. Data breaches damage trust and reputation, while supply chain incidents highlight hidden vulnerabilities. Beyond systems, attacks affect staff morale and leadership confidence.
A multi-layered defense strategy is essential to stop cyber threats. Businesses should use MFA, endpoint protection, SOC monitoring, audits, and secure backups. Employee training and awareness are key to preventing human-error-based attacks.
Building resilience requires step-by-step planning, from risk assessments to regulatory alignment with NCA, PDPL, and SAMA. A defense roadmap should cover security tools, employee training, monitoring, and recovery plans. Continuous audits and quarterly reviews help adapt security to evolving threats.
Aseef developed a secure fintech platform for Centurion Invest with real-time data, encryption, and compliance built in. The platform improved user engagement while ensuring top-level security. Within three months, it achieved zero incidents and a 30% increase in activity.
Frequently Asked Questions (FAQs)
1. Are Saudi businesses at risk of cyber attacks?
Yes. Cyber attacks in Saudi Arabia are rising, especially against SMEs and online platforms.
2. What is a physical attack in cyber security?
It involves tampering with hardware—like servers or USB ports—to gain access or cause damage.
3. Why do hackers target hardware in cyber security?
Hardware attacks bypass digital firewalls and can expose sensitive data physically stored on devices.
4. How can I prevent phishing attacks?
Train your staff, use email filters, and enforce two-factor authentication.
5. What are good cyber attack security solutions?
Firewalls, endpoint protection, MFA, real-time monitoring, and secure data backups.
6. How often should I audit my cybersecurity?
At least every 3–6 months or after major system updates.
7. Why choose Aseef for cyber security?
We offer local expertise, custom solutions, and compliance with Saudi NCA standards.
8. How fast can Aseef set up cyber security?
Initial assessment in 3–5 days, with full rollout based on your business needs.
Publication Date
Category
- Cyber Security
Table of Contents
Ready to Transform?
Whether you’re starting your digital journey or scaling transformation, Aseef is your reliable IT consulting company in Saudi Arabia.